
What is Tailgating in Cybersecurity? Risks and Prevention
Dec. 23, 2024
What if someone following an employee through a secure entrance could put your entire company at risk?
It may seem small, but this is precisely how tailgating attacks happen—and they’re becoming a bigger problem than many realize.
A recent survey found that almost half of respondents believe tailgating-related security breaches have increased over the past decade. Even more worrying is that over 70% said it’s very likely that a tailgating incident could take place at their workplace.
Regarding the cost of such attacks, the survey estimated that a serious tailgating incident—resulting in theft or violence—could cost over $150,000. Some even suggested that the damage, both financial and reputational, could be impossible to calculate.
While tailgating attacks may seem trivial initially, they can have far-reaching consequences for an organization’s security posture. So, how can you protect your business from this rising risk? This blog discusses tailgating attacks, common examples, tailgating vs piggybacking, how they occur, who is at risk, and how to prevent them.
What is a Tailgating Attack?
A tailgating attack is a physical security breach where an unauthorized individual gains access to a restricted area by following an authorized person. This often occurs in workplaces, data centers, or any facility where access is controlled by physical obstacles such as security doors, turnstiles, or keycard access systems. Tailgating exploits the trust and courtesy of employees who might hold the door open for someone or fail to verify their credentials.
As a managed security service provider (MSSP), we recognize that tailgating attacks represent a significant yet often underestimated risk to organizational security. Unlike cyberattacks that rely on technical vulnerabilities, tailgating exploits human behavior, making it particularly challenging to mitigate with standard IT solutions alone. This attack can compromise sensitive information, disrupt operations, or lead to further security breaches.
Tailgating vs Piggybacking: Understanding the Difference
When discussing physical security threats, “tailgating” and “piggybacking” are often used interchangeably. While they share a few similarities, these methods differ in context and execution.
Tailgating involves an unauthorized individual gaining access to a secure area by following an authorized person without explicit permission or knowledge. For example, an attacker may wait near an employee entrance and slip in as the door closes behind an authorized person, exploiting their distraction or the time lag of automated door mechanisms.
Tailgating is unnoticed access, where the authorized individual is unaware they have been followed.
Piggybacking, on the other hand, involves an unauthorized individual gaining access to a secure area with the consent or cooperation—intentional or not—of an authorized person. In many cases, the attacker manipulates the authorized person into granting access, often through social engineering techniques.
Someone might pretend to have forgotten their access card and ask an employee to hold the door open. In such cases, the authorized individual knowingly allows the person to enter but does so under the assumption that the individual is legitimate.
Piggybacking is, therefore, permitted access but based on false premises or misplaced trust.
Differences Between Tailgating and Piggybacking
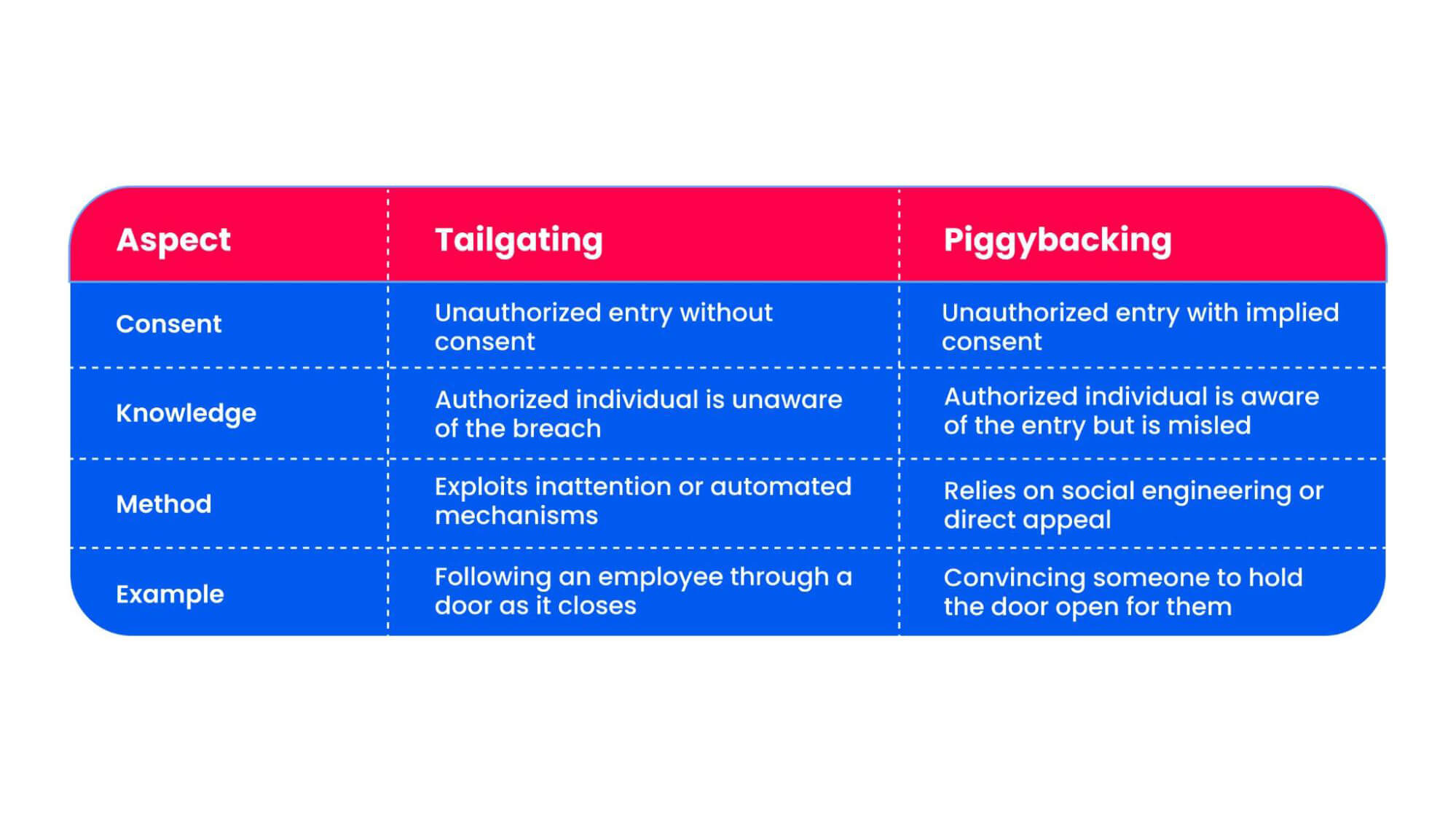
While tailgating and piggybacking are similar in their end goal—unauthorized access—their differences highlight multiple methods attackers may use to exploit physical security vulnerabilities. Recognizing the difference between these two allows enterprises to implement targeted strategies to mitigate risks effectively.
Common Examples of Tailgating
Here are some typical scenarios where tailgating can occur:
Following Through an Access-Controlled Door
One of the most common examples of tailgating is when an unauthorized person slips through a door that requires a keycard, fob, or PIN. This often happens in busy areas, such as office lobbies or parking garages, where employees enter and exit frequently. The attacker might closely follow an authorized person, timing their movements to prevent other employees from getting suspicious.
Exploiting a Distracted Employee
Employees preoccupied with tasks, conversations, or carrying items are more likely to leave doors open for longer than necessary. An attacker can use this moment of distraction to gain access without being noticed.
Taking Advantage of Courtesy
People are naturally inclined to hold doors open for others, especially in professional or polite environments. An attacker might approach someone entering a secure area, carrying items to appear as though they need assistance, or simply walking closely behind them. The employee may assume the individual belongs there and hold the door open, unknowingly allowing them inside.
Blending in During High-Traffic Times
Busy times like shift changes or lunch hours are prime opportunities for tailgaters. In these moments, there’s a steady flow of people entering and exiting secure areas, and security personnel may have difficulty monitoring everyone. Attackers can easily blend in with the crowd and follow an employee through an access point.
Disguising Intent with Small Talk
An attacker might casually converse with an employee to build rapport and lower suspicion. For example, they might strike up a friendly chat in the elevator and then casually follow the employee into a secure area.
Tailgating Via Delivery or Maintenance Personas
Attackers might pose as delivery personnel, repair technicians, or maintenance workers who “need access” to complete a job. Employees may feel pressured to assist due to the appearance of urgency or legitimacy in these roles.
These examples demonstrate how tailgating can take on various forms. Hence, awareness and vigilance are crucial for preventing tailgating. By understanding these scenarios, businesses can prepare employees and implement security measures to minimize risks.
Who is Most at Risk for Tailgating Attacks?
While anyone can fall victim to these attacks, here are a few types of employees who may be more vulnerable than others:
- New Employees:Unfamiliar with coworkers and security protocols, they may hesitate to question someone following them.
- High-Turnover Roles:Frequent staff changes create a relaxed security culture where unfamiliar faces are common.
- Polite or Trusting Employees:Courteous individuals might hold doors open for strangers, unwittingly assisting attackers.
- Distracted Employees:Preoccupied with tasks or devices, they may fail to notice unauthorized individuals tailgating them
- Senior Executives:Their high-level access makes them valuable targets, though they are often more aware of risks.
How Do Tailgating Breaches Impact Enterprise Security?
Tailgating breaches may seem minor, but they pose serious risks to enterprise security. Here’s how these incidents can impact organizations:
Physical Security Gaps
Many companies focus heavily on digital security (firewalls, encryption, and secure access controls) but neglect physical security, which is just as important. Tailgating attacks exploit these gaps in physical security. If employees aren’t vigilant about who follows them into secure areas, malicious actors can easily slip through the cracks without triggering any alarms. These low-tech breaches make them harder to detect and mitigate until too late.
Access to Sensitive Areas
Once inside, tailgaters can access critical areas containing confidential data, intellectual property, and essential business resources. This could include server rooms, R&D departments, financial records, or employee areas where sensitive information is stored. Even if cybersecurity measures are in place, physical access allows attackers to bypass these digital protections, potentially exposing the business to theft or tampering.
Threats to Confidentiality
Tailgating often exposes sensitive data. Unauthorized individuals may steal physical documents or digital information by accessing servers or computers. They could also install devices like keyloggers or network sniffers to collect data over time. This breach of confidentiality can result in data leaks, intellectual property theft, and long-term financial damage. Additionally, once sensitive information is compromised, it can lead to a loss of customer trust, legal action, and financial penalties.
Cybersecurity Compromise
Physical access to an enterprise’s infrastructure paves the way for cybersecurity threats. Attackers who gain entry through tailgating can attempt to plug into the network, steal employee credentials, or introduce malware. This physical breach could provide access to other network entry points—such as wireless access points or network terminals—and compromise an organization’s IT defenses. Once inside, the attacker could execute more damaging cyberattacks like ransomware, spyware, or data exfiltration.
Undermines Security Culture
If organizations allow tailgating to occur regularly, it can erode their security culture. If employees get used to letting others follow them into secure areas, they may overlook the importance of staying vigilant. This can lead to a more relaxed attitude toward security, which makes it easier to ignore other important security policies. As a result, the organization becomes more vulnerable to future breaches, both physical and digital.
Insider Threats
Tailgating exposes a business to external threats and can also enable insider threats. A dissatisfied employee, contractor, or malicious insider could exploit weak physical access controls to gain unauthorized entry and execute harmful actions. Whether stealing sensitive information, sabotaging systems, or engaging in corporate espionage, a tailgating breach makes it easier for insiders to act without suspicion.
How to Prevent Your Business from Tailgating Attacks
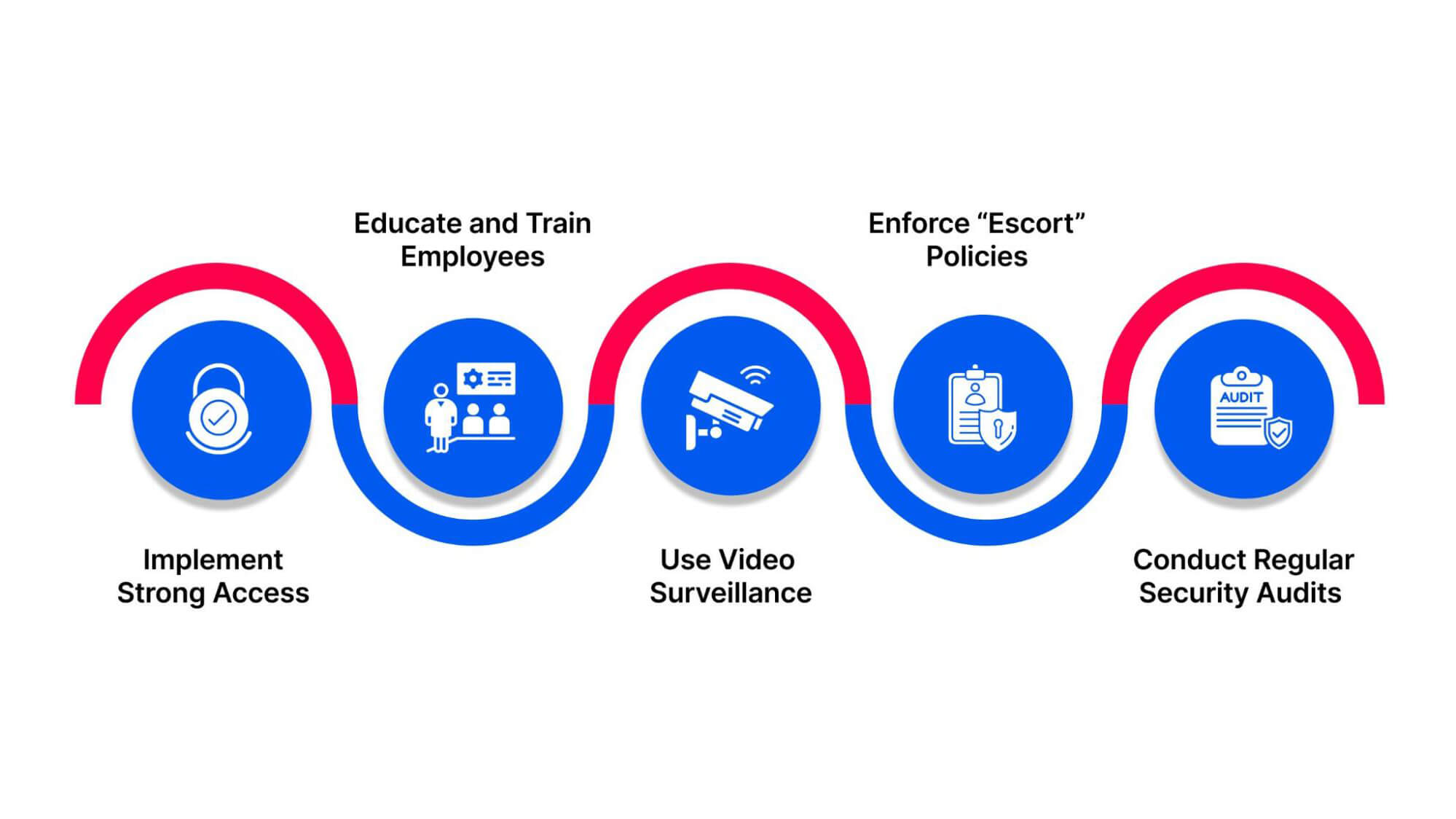
As a Managed Security Service Provider (MSSP), we understand that installing the right security systems to prevent a tailgating attack is not enough; you need to cultivate a security-first culture across your organization. Here are a few steps to minimize the risk and safeguard your business from these threats:
Implement Strong Access
The first line of defense against tailgating is a powerful access control system. This includes installing security barriers such as turnstiles, card readers, or biometric scanners that prevent unauthorized individuals from entering secure areas. Each person must have unique access credentials, which helps prevent employees from using each other’s credentials to get in. Additionally, these systems should be regularly monitored to ensure they’re working properly and detect any issues before they become problems.
We recommend that businesses deploy multi-factor authentication (MFA) for physical access in high-security zones, which adds an extra layer of protection. Employees must swipe access cards or use biometric verification with PIN codes or facial recognition. This makes it significantly harder for an attacker to follow an authorized person into restricted areas.
Educate and Train Employees
Human error is often the most significant vulnerability in tailgating attacks, so training your employees is essential. They need to understand the risks associated with tailgating and be able to recognize and respond appropriately. Employees should be taught not to hold doors open for strangers, even if they appear to be legitimate workers or visitors. You must encourage a “no tailgating” policy, where employees are empowered to question or challenge unfamiliar individuals, which can significantly reduce the chances of an attacker sneaking in.
We work closely with our clients to provide ongoing security awareness training, including practical scenarios and best practices for preventing tailgating. This training should be reinforced regularly so that employees stay alert and understand the consequences of complacency.
Use Video Surveillance
Another effective measure to prevent tailgating is using video surveillance cameras in and around access points. Surveillance helps security teams monitor who is entering and exiting secure areas. Cameras can be strategically placed near doors or elevators, and footage can be analyzed to identify potential instances of tailgating.
Additionally, video monitoring must be combined with real-time alerts. This allows your security team to respond immediately if they spot an unauthorized entry attempt rather than waiting for an incident to be discovered later. Recorded footage can also be invaluable in investigating any security breaches or incidents.
Enforce “Escort” Policies
An escort policy must be in place for visitors, contractors, or anyone without authorized access to certain areas. Visitors must be escorted by an authorized employee while in restricted zones. By ensuring that all guests are monitored, you minimize the risk of tailgating.
Visitors must also be clearly identifiable—using badges or visitor passes that distinguish them from regular employees. This makes it easier for staff to spot someone trying to sneak into a restricted area.
Conduct Regular Security Audits
Conduct physical security audits to ensure access control systems are up to date and functioning properly. This includes reviewing access activity logs and checking that only authorized personnel can enter restricted areas.
In addition, run tailgating-specific drills with your staff. Simulated scenarios can help employees practice identifying tailgaters and responding appropriately. Drills raise awareness and ensure everyone knows how to act in real-world situations, making it less likely that they will become complacent or fail to notice suspicious behavior.
Monitor Physical Access Logs
It’s essential to keep detailed logs of physical access events. These logs should include information about who enters secure areas, when, and why. Monitoring these logs regularly helps security teams track patterns and identify any anomalies that could indicate a tailgating attempt. Automated systems can even flag suspicious activity, like multiple failed access attempts or entries during off-hours, which can then be investigated.
Prevent Tailgating Attacks with STACK Cybersecurity

STACK Cybersecurity partners with clients to provide comprehensive protection against cyber threats.
What We Offer
- Tailgating Prevention Solutions: We understand the importance of securing your physical and digital assets. Our team works closely with clients to implement access control strategies and enhance physical security to prevent tailgating attacks.
- Comprehensive Risk Management: We provide end-to-end cybersecurity services, including threat detection, response, and continuous monitoring to minimize your exposure to tailgating and other physical security breaches.
- Security Awareness Training: We help train your employees to recognize and respond to tailgating attempts, nurturing a culture of vigilance and proactive security.
- Compliance Support: We help your business meet industry regulations like CMMC and SOC 2 Type 2.
Enhance Your Security Today
At STACK Cybersecurity, we help you build a multi-layered defense against tailgating and other security threats. Trust us to safeguard your organization from the inside out—protecting your physical spaces and sensitive data.
Let’s work together to strengthen your cybersecurity posture. Schedule a Consultation
