Typosquatting: The Hidden Threat in a Mistyped URL
April 2, 2025

A single mistyped character in your web address can lead visitors into a carefully crafted trap. Behind these seemingly innocent typing errors lies a sophisticated cyber threat: typosquatting. This practice has evolved from simple web address tricks to become a serious security concern.
What is Typosquatting?
Typosquatting (also known as URL hijacking) occurs when hackers register domain names that are slight variations of legitimate, popular websites. These domains capitalize on common typing errors users make when entering web addresses.
For example, a user intending to visit "example.com" might accidentally type any of the following variations:
- exmaple.com (transposed letters)
- exampl.com (missing letter)
- examplecom.com (missing dot)
- example.org (wrong TLD)
Cybercriminals register these variations and create sites that mimic the legitimate website, often with the goal of harvesting credentials, distributing malware, or committing fraud.
Real-World Example: Anatomy of a Typosquatted Domain
Here's a fictional example of how typosquatting looks in practice. This is the type of domain information STACK Cybersecurity uncovers for clients during threat intelligence investigations.
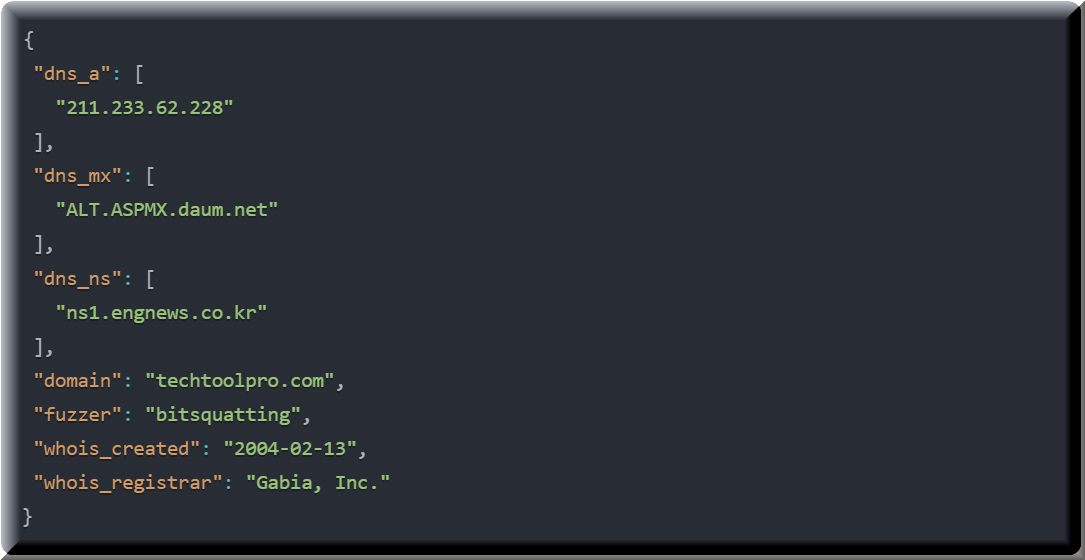
This data reveals several interesting points. The domain was identified through "bitsquatting" - a sophisticated form of typosquatting that targets bit-level errors in memory or transmission. It was registered back in 2004, showing how long-standing this practice can be. The domain uses Korean nameservers and a Korean registrar (Gabia). The mail exchanger points to Daum, a Korean web portal and email service.
In this case, the typosquatted domain "techtoolpro.com" might be targeting users attempting to reach the legitimate "techtoolspro.com" (notice the missing 's'), a fictional industrial equipment manufacturer.
The Business Impact of Typosquatting
The consequences of typosquatting extend beyond user inconvenience. Credential theft occurs when users unwittingly enter their login information on a malicious site that appears legitimate. These fake sites often distribute malware through downloads. Brand reputation suffers when users have negative experiences on fraudulent sites they believe to be authentic. Companies also face revenue loss when competitors use typosquatted domains to redirect potential customers to their services.
STACK Cybersecurity's Domain Monitoring Capabilities
At STACK Cybersecurity, we employ advanced scanning technology to identify typosquatting threats for our clients. In a recent scan for one of our clients, we discovered more than 10 alternate URLs targeting their brand. Our comprehensive domain monitoring service helps businesses identify these threats before they can be exploited.
Our scanning capabilities allow us to identify registered domains that are potential typosquatting threats, analyze the technical infrastructure behind suspicious domains, monitor for changes in ownership or website content, and provide actionable intelligence to mitigate risks.
Finding Your Typosquatting Exposure
Identifying potential typosquatting targets for your domain is a valuable part of your threat intelligence program. Generate common typos using pattern-based approaches such as character omission, duplication, adjacent character substitution, transposition, homoglyph substitution, and bitsquatting. Then verify which variants are already registered and active.
Examine DNS records, hosting locations, and other technical indicators to identify suspicious patterns. Finally, track changes in DNS settings and website content that might indicate a domain has been repurposed for malicious use.
Defensive Strategies
Protecting your corporation against typosquatting requires a multi-layered approach, including the following tactics.
- Proactively register common misspellings of your domain name
- Implement continuous monitoring for new lookalike domain registrations
- Use legal mechanisms like trademark complaints and UDRP (Uniform Domain-Name Dispute-Resolution Policy) to take down infringing domains
- Teach your users about the risks of typosquatting and encourage the use of bookmarks or links from official communications
- Implement email authentication protocols like DMARC, SPF, and DKIM to prevent email spoofing from lookalike domains
Turn Typosquatting into Threat Intelligence
The patterns of typosquatting attempts against your domain can provide valuable intelligence about threat actors targeting your business. Consider which domains are being targeted most frequently, what techniques are being employed, whether there are patterns in registration timing that might indicate coordinated campaigns, and if you can identify the threat actors based on infrastructure reuse or tactics. This intelligence can help inform your broader security strategy and resource allocation.
Looking Ahead
Typosquatting represents a significant but often overlooked cybersecurity risk. By understanding how adversaries exploit human error in web address entry, you can better protect your users and your brand reputation. Implementing a proactive monitoring and defense program against lookalike domains should be an essential component of your firm's security posture.
In cybersecurity, sometimes the smallest mistakes, like a single mistyped character, can lead to the biggest vulnerabilities.
Follow STACK Cybersecurity on LinkedIn.
Cybersecurity Consultation
Do you know if your company is secure against cyber threats? Do you have the right security policies, tools, and practices in place to protect your data, reputation, and productivity? If you're not sure, it's time for a cybersecurity risk assessment (CSRA). STACK Cybersecurity's CSRA will meticulously identify and evaluate vulnerabilities and risks within your IT environment. We'll assess your network, systems, applications, and devices, and provide you a detailed report and action plan to improve your security posture. Don't wait until it's too late.
