Is Your Company Ready to Lose Defense Contracts?
Dec. 12, 2025
The Clock Ran Out
On Nov. 10, 2025, the Department of Defense (DoD) started implementing the Cybersecurity Maturity Model Certification (CMMC) 2.0 Program by directing contract officers to add the updated Defense Federal Acquisition Regulation Supplement (DFARS) clause to applicable new contracts and renewals. This launched a three-year phased rollout, making CMMC requirements increasingly common in solicitations until they become standard for most defense contracts.
CMMC was first introduced in January 2020.
The program has gone through significant changes since then:
- January 2020: CMMC 1.0 announced (had 5 levels)
- November 2021: CMMC 2.0 announced (simplified to 3 levels)
- December 2023: CMMC 2.0 proposed rule published in Federal Register
- October 2024: Final CMMC rule published
- November 10, 2025: Implementation began with updated DFARS clause
After years of delays and changes, cybersecurity is no longer a back-page requirement. It’s part of the contract conversation from the very beginning.
Defense contractors have had nearly six years since the initial announcement to start preparing, and about four years since CMMC 2.0's structure was established.
For contracts where the CMMC clause applies, defense suppliers that don’t meet the required certification level can’t be considered eligible for award or renewal. Over time, that will directly affect a company’s ability to keep its place in the defense supply chain.
This shift is reshaping the Defense Industrial Base (DIB), which includes hundreds of thousands of businesses across the country. The message from the Pentagon is straightforward: if you want to handle Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) for DoD, you need to prove you can protect it.
Learn more: https://dodcio.defense.gov/cmmc/About/
The urgency is rooted in how modern conflict actually works.
‘Adversarial Asymmetric Warfare’
"We are in an era of adversarial asymmetric warfare for which we have no comprehensive deterrence," warned a 2018 MITRE study commissioned by the DoD. The report highlighted that adversaries don’t need to attack the United States directly. Instead, they can target vulnerable supply chains, cyber infrastructure, and people to quietly degrade national capabilities before they’re ever used.
MITRE is a not-for-profit corporation that operates federally funded research and development centers (FFRDCs) for the U.S. government. MITRE's independence and technical credibility make them a trusted source for this type of strategic analysis, which is why their warning about adversaries targeting vulnerable supply chains carries significant weight.
The fact that MITRE identified these supply chain cybersecurity risks back in 2018 provides additional context for why CMMC became necessary: the threat assessment came from one of the government's most trusted technical advisory bodies.
What Nov. 10 Changed
The updated DFARS 252.204-7021 clause will now be added to applicable solicitations and contracts, giving contracting officers the authority to make CMMC compliance a condition of award.
CMMC 2.0 has three levels, aligned to the sensitivity of information you handle.
Level 1 (Foundational) requires self-assessment for contractors handling FCI. The baseline includes 17 basic security practices covering access control, identification, authentication, media protection, and physical safeguards.
Level 2 (Advanced) mandates implementation of all 110 National Institute of Standards and Technology (NIST) Special Publication 800-171 controls. Depending on contract sensitivity, companies must either self-assess or undergo third-party audits to verify compliance. This verification requirement represents a shift from previous trust-based approaches. Now the DoD gets assurance suppliers have implemented required cybersecurity standards on non-federal information systems processing, storing, or transmitting Controlled Unclassified Information (CUI).
Level 3 (Expert) involves government-led assessments reserved for the most critical defense programs. This tier applies to fewer than 10% of DoD contractors.
Rollout Timeline
CMMC enforcement is phased:
- Nov 2025–Nov 2026: Level 1 and Level 2 self-assessments appear in applicable contracts.
- Starting Nov 2026: Third-party Level 2 assessments become more common.
- Starting Nov 2027: Government-led Level 3 assessments begin.
- By Nov 2028: DoD expects full implementation across applicable contracts.
For contractors, the window to prepare is narrowing quickly.
Many Prime Contractors Take Action
Major defense primes are already pushing compliance requirements down their supply chains. In a letter to suppliers, Leonardo DRS notified vendors that CMMC Level 2 requirements certified by a third-party Certified Third-Party Assessor Organization (C3PAO) could appear in contracts "at any point within the next 2 years."
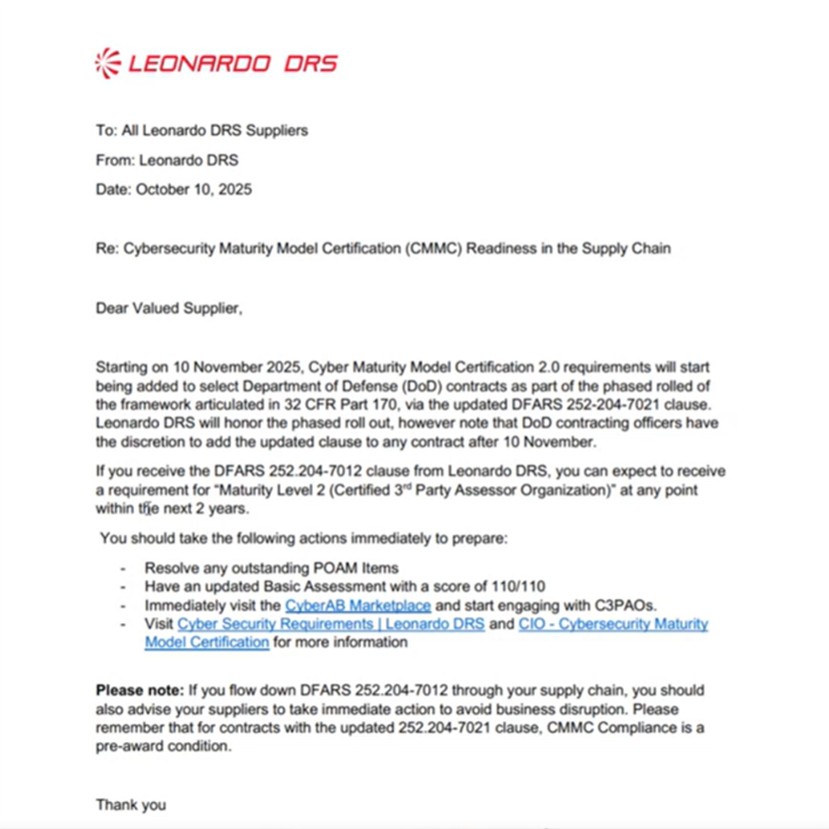
The letter outlines specific preparation steps, including resolving outstanding Plan of Action and Milestones (POA&M) items, achieving a 110/110 score on Basic Assessment and immediately engaging with C3PAOs. Leonardo DRS explicitly stated that CMMC compliance is a pre-award condition and urged suppliers to notify their own sub-tier vendors to avoid business disruption.
This flow-down pressure illustrates the cascading impact across the defense industrial base (DIB). The CMMC program formalizes protection requirements that flow down to subcontractors at every tier. Companies must achieve the specified CMMC level as a condition of contract award, even if they never contract directly with the DoD.
Subcontractors handling FCI or CUI face the same verification requirements as prime contractors.
Primes Struggle As Well
Even small prime contractors with decades of defense industry experience are scrambling to achieve certification, hiring new staff solely to navigate the compliance process. Many small prime contractors are only now consulting The Cyber AB website in search of Registered Practitioner Organizations (RPOs) to manage their compliance projects.
The Cyber AB is the official accreditation body of the CMMC ecosystem.
In a recent consultation with an RPO, a newly hired compliance administrator at a one-person prime contractor repeatedly expressed confusion about basic CMMC supplier notification processes, saying "I'm not understanding your questionings" when asked whether the firm had received or issued compliance letters to its supply chain.
Despite the owner's extensive background with major defense contractors, including Science Applications International Corporation (SAIC), the administrator acknowledged IT security requirements were simply "not his forte." The firm needs Level 2 certification "as soon as possible" but struggled to articulate its compliance status or supply chain position.
The exchange illustrates a troubling reality: even contractors with deep operational military knowledge find themselves lost in CMMC's technical requirements. Cybersecurity compliance represents a distinct skill set from defense contract management, and the knowledge gaps extend throughout the entire supply chain, regardless of company size or experience level.
Cost of Delay
Defense industry experts predict the DIB could shrink by 40% or more as CMMC requirements take effect. While some businesses will exit defense contracting entirely, others see this consolidation as creating opportunity.
One Michigan manufacturer reported in September that after achieving compliance, their workload increased dramatically when a client lost 80% of their supplier base to companies unable or unwilling to meet certification requirements.
Delaying CMMC preparation introduces several risks:
- Higher costs for expedited assessments
- Loss of contract opportunities
- Reputational damage inside your supply chain
- Legal exposure from inaccurate self-attestation or outdated compliance scores
Enforcement Consequences
The Department of Justice has made it clear: cybersecurity misrepresentations are a False Claims Act issue.
A recent case involving MORSECORP Inc. illustrates the consequences. The Massachusetts contractor settled for $4.6 million after misrepresenting its NIST SP 800-171 implementation score. A third-party consultant found the company's actual score was -142, despite MORSECORP having reported 104. The company delayed updating its score for nearly a year and did so only after receiving a subpoena.
The settlement included $2.3 million in restitution and an $851,000 whistleblower award.
The case demonstrates that inaccurate self-reporting carries severe consequences beyond technical remediation costs. Contractors who submit payment requests while knowing they haven’t met contractual cybersecurity requirements face significant legal exposure.
Learn more about the case: https://stackcybersecurity.com/posts/false-claims
Evolving Requirements
CMMC is closely tied to NIST standards, which continue to evolve.
- NIST SP 800-171 Rev. 3 is now final, introducing new structure and organization-defined parameters. https://csrc.nist.gov/pubs/sp/800/171/r3/final
- NIST SP 800-172 provides enhanced protection for high-value CUI environments. https://csrc.nist.gov/Pubs/sp/800/172/Final
- NIST SP 800-172 Rev. 3 is currently in draft. https://csrc.nist.gov/pubs/sp/800/172/r3/fpd
Future CMMC updates are expected to align with these revisions, meaning compliance will remain a continuous improvement effort rather than a one-time milestone.
As former Defense Security Service Director William Stephens noted, DoD’s goal is to deliver warfighting capability without allowing critical information to be “lost, stolen, denied, degraded, or inappropriately given away or sold.”
That mission is driving DoD to treat cybersecurity as equal in importance to cost, schedule, and performance.
The Knowledge Gap Crisis
The confusion extends beyond understanding CMMC's technical requirements. In preparation for a recent consultation, a small prime contractor submitted a written overview of its current security posture that revealed alarming misconceptions about both its compliance status and cybersecurity.
The firm stated it had "completed CMMC lvl1 Self Certification" but in the same message acknowledged they "have not completed any NIST 800-171 or CMMC self-assessments." You cannot have completed Level 1 certification AND not have completed any assessments. That's not a minor confusion; it's a fundamental misunderstanding of what certification means.
They described a disabled veteran handling CUI for weapon and biological systems from his private residence, protected by a consumer-grade VPN service typically marketed to individuals concerned about streaming geo-restrictions.
Weapon systems data. Biological systems data. In a residence. With a $12 a month VPN as the protection layer. This is akin to using a bike lock on a bank vault.
The contractor needed Level 2 certification within two months but was still "getting quotes" for basic firewall infrastructure.
These aren't edge cases. Similar patterns appear throughout the defense supply chain: contractors with legitimate defense work, handling genuine CUI, operating under fundamental misunderstandings about what compliance requires and what security they have.
The RPO Solution
Most defense contractors don’t have internal CMMC experts. That’s where Registered Practitioner Organizations (RPOs) come in.
CMMC RPOs help defense contractors:
- Interpret requirements
- Build System Security Plans
- Design compliant system boundaries
- Implement controls efficiently
- Prepare for assessments
Modern defense environments are software-driven. A single aircraft can contain over 10 million lines of code, and certain F-35 variants exceed 20 million. Each integration point and line of code represents a potential attack surface if not secured properly.
RPOs treat compliance as a structured project rather than a one-off technical task, coordinating the policy, technical, and operational work needed to reach certification.
STACK Cybersecurity, a Livonia, Mich.-based CMMC RPO, serves manufacturers, defense contractors, and compliance-focused businesses across the country. As both a managed service provider (MSP) creating IT infrastructure and a managed security service provider (MSSP) protecting it, STACK holds credentials including Service Organization Control (SOC) 2 Type II certification that demonstrates their own security maturity.
“A lot of manufacturers still rely on outdated systems and tribal IT knowledge,” said Rich Miller, founder and CEO of STACK Cybersecurity. “That era is over. CMMC forces companies to rebuild on solid, secure foundations — and the ones who refuse are going to lose contracts to those who do.”
Common Misunderstandings
Even Level 1 can be deceptively challenging. Frequent stumbling points include:
- Maintaining a complete asset inventory
- Enforcing least privilege
- Implementing MFA everywhere it belongs
- Ensuring reliable, tested backups
CUI marking mistakes are also widespread. Some companies label everything as CUI, including routine emails, while others fail to label actual CUI. Over-marking creates unnecessary workload. Under-marking creates exposure.
Physical security is another common gap. Companies have passed paperwork reviews only to fail in-person assessments due to visitor management issues, unlocked doors, or unmonitored access points.
The Starting Gun
CMMC represents more than another regulatory acronym. The Nov. 10 deadline marked the beginning of a new business reality for defense contractors. Companies that act decisively will secure their market position, strengthen their security posture, and protect their place in the defense supply chain.
The phased rollout provides a window for preparation, but that window is closing.
Defense industry professionals draw parallels to previous quality management transitions. When ISO 9001 and AS9100 standards emerged, companies initially resisted the costs and perceived bureaucracy. Then these certifications became standard business requirements that no one questioned.
Industry experts predict CMMC will follow the same trajectory.
“CMMC is no longer a technical project,” Miller said. “It’s a business survival project. The companies treating this like a strategic investment are the ones that will still be in the defense supply chain three years from now.”
