Digital Credential Essentials
Nov 16, 2024

A verifiable digital credential (VDC) is a tamper-evident digital document that contains information about an individual, organization, or asset, and is issued by an authoritative source. VDCs are digital representations of physical credentials, such as driver's licenses or diplomas, that can be stored in a digital wallet and cryptographically verified.
The global issue of forged physical and digital credentials is growing, making the verification process slow, time-consuming, and costly for organizations. VDCs offer a solution by providing a digital, cryptographically secured version of credentials that can be verified.
In the VDC ecosystem, there are three key roles: issuer, holder, and verifier. Issuing organizations can create fraud-proof digital credentials, while verifying organizations can instantly authenticate them. This system gives individuals ownership and control over their data, enhancing privacy and security.
VDCs have a wide range of applications across various sectors, including supply chain, education, and finance, demonstrating their versatility and potential to streamline the credential verification processes.
These more secure credentials are gaining popularity globally because they meet key user privacy requirements and tackle several significant issues in the current identity management system. Their ability to enhance privacy, security, and control over personal data makes them an attractive solution for both individuals and businesses.
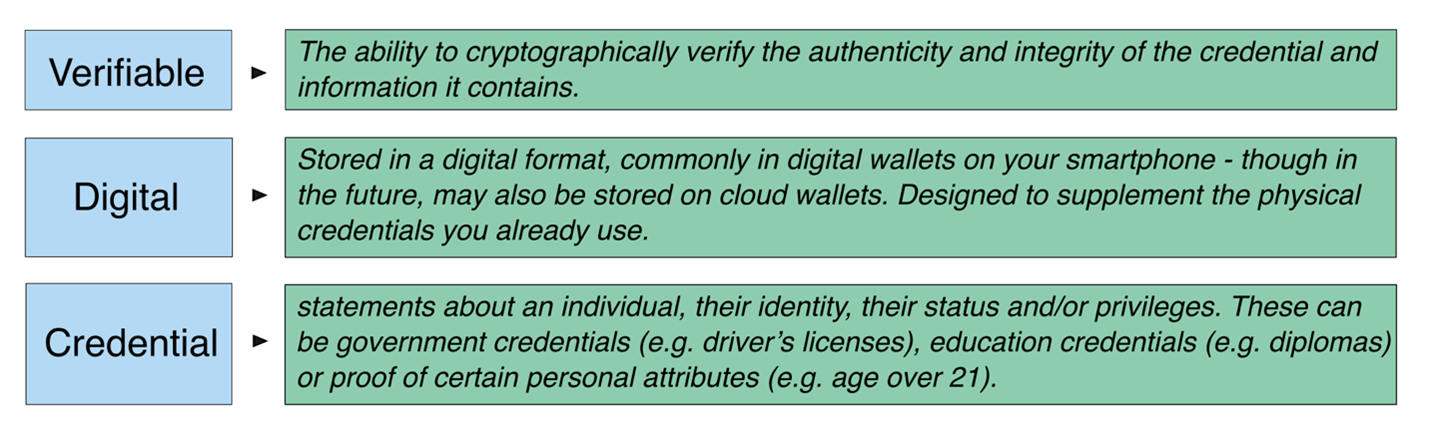
Features that enable identity verification and authentication include:
- Cryptographic Security: VDCs use public key cryptography to digitally sign the credential, ensuring its integrity and authenticity.
- Tamper-Evidence: Any attempt to modify the contents of a VDC can be detected, as the digital signature will no longer match the credential's data.
- Selective Disclosure: VDCs allow users to share only the necessary information, without revealing the full set of personal data.
- Revocation and Updates: VDCs can be revoked or updated by the issuing authority, enabling effective credential lifecycle management.
- Offline Verification: VDCs can be verified without the need for a constant internet connection or access to a central database.
These features make VDCs a valuable tool for enhancing identity verification and authentication in digital environments, contributing to improved security and trust in online transactions and interactions.
Cryptographic security safeguards information from unauthorized access, modification, or destruction through techniques like encryption. Public-key cryptography, which uses a pair of keys (one public, one private), ensures secure communication and supports digital signatures to verify the authenticity and integrity of messages. This method is integral to secure internet protocols like SSL/TLS.

Primary Components of the VDC Ecosystem
- Digital Wallet: A mobile app that holds and secures VDCs.
- Issuer: The entity that provisions and cryptographically signs the VDC.
- Verifier: The entity responsible for verifying the authenticity and integrity of the VDC.
- Relying Party: The entity that relies on the verifier's assertion of the VDC to grant access or process a transaction.
- Trust Service: A centralized service that enables relying parties to access cryptographic keys from multiple issuers.
Although digital credentials provide better security than traditional ones, they still face cybersecurity threats. Cybercriminals might try to tamper with these credentials or exploit system vulnerabilities, putting both individuals and organizations at risk.
Even with privacy-preserving designs, VDCs still raise data privacy and surveillance concerns. Without proper safeguards, there's a risk sensitive information could be exposed or misused.
Even though open standards for VDCs exist, achieving widespread adoption and interoperability across various systems and platforms remains challenging. Different implementations and competing standards can impede the scalability and effectiveness of digital credentialing efforts.
Potential cybersecurity challenges with VDCs include:
- Secure storage and management of digital credentials: Ensuring the secure storage of VDCs in digital wallets and preventing unauthorized access or theft of these credentials is crucial.
- Vulnerability to cyberattacks: VDC infrastructure and associated applications and services could be vulnerable to cyberattacks, such as hacking, phishing, or malware, which could compromise the integrity of the credentials.
- Privacy and data protection concerns: The collection and storage of personal information within VDCs raise privacy concerns, and appropriate data protection measures must be implemented to safeguard user privacy.
- Interoperability and standardization: Ensuring seamless interoperability between different VDC systems and adherence to common standards is essential to prevent fragmentation and enhance widespread adoption.
- Scalability and performance: As the use of VDCs grows, the underlying infrastructure must be able to handle increasing volumes of transactions and users without compromising security or performance.
Verifiable digital credentials have the potential to revolutionize identity management and authentication, providing enhanced security, efficiency, and privacy. However, they also come with challenges such as technical complexity, accessibility issues, security risks, privacy concerns, and the need for standardization. Overcoming these challenges will be essential to fully realizing the benefits of digital credentialing in the future.
Mobile Driver's License Research
The National Cybersecurity Center of Excellence (NCCoE), part of the National Institute of Standards and Technology (NIST), wants to accelerate the adoption of mobile driver’s license standards and best practices. Along with many collaborators, NCCoE will build a reference architecture demonstrating business cases to integrate mDLs with commercially available technologies. Read the MDL Fact Sheet
Need help improving your cybersecurity posture?
Call (734) 744-5300 or Contact Us to learn how our Cyber STACK can fortify your defenses.
